What is ATM jackpotting attack
2022-05-04ATM Jackpotting Attack
We all know the pleasant sound of ATM bills counting down. But it’s even more satisfying to pick them up from an ATM. This is a sensation pursued by many attackers who conduct targeted attacks on ATMs. One such attack is ATM jackpotting.
ATM jackpotting is the installation and activation by criminals of malicious software on an ATM that triggers the withdrawal of all cash. Such attacks first became known in January 2018. The representatives of Diebold Nixdorf Inc and NCR Corp, two of the world’s largest ATM manufacturers, warned users about the cybercrime.
Today we will tell you what ATM jackpotting is and how to avoid attacks. You will also learn about the peculiarities of malware and software.
Contents
What is ATM jackpotting
ATM jackpotting is a type of attack in which hackers connect to the particular ATM and give it a sequence of commands to dispense all the money from the built-in safe. This type of hacking scheme of the ATM security system in order to intercept the cash withdrawal control can be done by compromising the bank software or by using special equipment.
The name of this type of attack comes from the word «jackpot», because the perpetrator in case of a successful hack gets all the money that was loaded into the ATM. After the ATM ejects all the cash accumulated inside, the perpetrator only has to put up a money bag and retrieve the loot.
Important: ATM jackpotting is not the easiest and most convenient way to get rich. First, need physical access to the ATM, the ability to connect to it and crack the basic security. Second, the process takes time, and ATMs are rarely located out of sight of security guards or surveillance cameras.
Often, cybercriminals entrust the receipt of money to low-skilled crooks called mules. These criminals are only tasked with collecting the cash and handing it over to the organizers of the attack.
Type of jackpotting attacks
In jackpotting, criminals exploit the ATM hardware and software vulnerabilities to abscond with cash. Criminals can disguise themselves as bank staff to easily gain access to the ATM. The most vulnerable to such attacks are considered freestanding ATMs that are within video surveillance distance.
Below we will describe the basic type of attacks by jackpotting.
Malware
Malware is capable of causing serious damage to a bank’s reputation and financial stability. This software allows fraudsters to force ATMs to dispense cash without reflecting withdrawals on any bank accounts.
The most famous malware:
Ploutus
Ploutus was discovered in Mexico. To install the first version of the program, a CD-ROM had to be inserted in the ATM CD-ROM. The next version was distributed via cell phone. To install the latest version of Ploutus (Ploutus-D) requires physical access to the top of the particular ATM.
Cutlet Maker
Before free distribution, Cutlet Maker could only be purchased online. This malware infects ATMs via a USB drive. Once Cutlet Maker has been installed, an image of a chef and a piece of meat appears on the ATM screen, along with the words “Ho-ho-ho-ho! Let’s make some cutlets today!”.
Black box
The Diebold Nixdorf ATM manufacturer first warned about the black box attack.
In this type of attack, intruders detach the external casing of an ATM to gain access to its ports. Attackers can also cut a hole in the casing to gain direct access to internal wiring and other hidden connectors. The attacker then connects a device called a “black box” (usually a laptop or Raspberry Pi board) to the ATM’s internal components, which are used to send commands and steal money. This method is popular among fraudsters because of its low cost and ease of implementation.
How jackpotting attacks work
In a robbery, attackers perform several actions. First of all, criminals gain access to local devices. Cybercriminals connect USB to ATM by means of a screwdriver. Once connected to the USB port, malicious code is injected into the ATM system. Finally, the ATM is rebooted to standard mode and then comes under the control of the malware. The last step is to steal the cash.
A step-by-step jackpotting scheme is shown below.
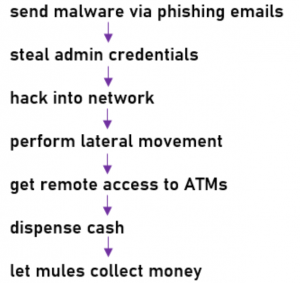
Recently, attackers prefer to attack ATMs with malware rather than by physical attack. This is due to the greater security of the procedure.
History of ATM jackpotting
In 2010, Barnaby Michael Douglas Jack, a New Zealand programmer, hacker, and electronic security researcher, made an ATM machine spit out the stream of dollar bills on stage at the Black Hat conference. This attack technique has been dubbed “jackpotting.”
According to the report by the European ATM Security Group, global losses from ATM fraud rose 18 percent to 156 million euros in the first half of 2015 compared to the same period in 2014. Meanwhile, most ATM malware attacks are concentrated in Europe.
In November 2016, the FBI issued a warning about an attack on the U.S. financial sector through jackpotting.
In the first half of 2019, criminal gangs managed to obtain 1,000 euros on only one successful robbery.
In 2020, ATM jackpotting was identified as a globally recognized problem.
In 2021, it became known about the arrest of two attackers from Belarus, who attacked European ATMs and received about 230,000 euros.
Jackpotting has been on the rise globally in recent years, although it is not known exactly how much cash was stolen because victims and police often do not disclose details. The total damage from all the hacks is unknown, but CNN estimates it was more than $1 million in the U.S. alone.

ATM security solutions
Banks wishing to protect their ATMs from jackpotting should:
- install and maintain antivirus software;
- disable auto-start and boot functions;
- make sure that default passwords are not set in ATMs;
- implement hard drive encryption mechanisms;
- provide a secure connection to the host using TLS and message authentication code;
- use two-factor authentication and track transactions by issuing code signatures and user keys to customers;
- limit physical access to the ATM by means of additional locks and video surveillance;
- use the most secure encrypted communication protocols;
- maintain the operating system and software stack up to date.
Important: At the recent 25th Meeting of the EAST Expert Group on All Terminal Fraud (EGAF), it was noted that the number of malware installations decreased by 74% and the number of fraudulent attacks decreased by 24%.
ATMeye.iQ can provide comprehensive protection against jackpotting and other types of fraud. This software solution greatly simplifies the work of a bank’s security service and allows to analyze photos and videos from surveillance cameras in real-time. ATMeye.iQ has special sensors that detect any suspicious actions: the sensor that detects camera closure, triggers, anti-camera, gas, tilt, and shock. When misconduct is detected, the system sends a notification, and security personnel can instantly respond to the threat through special scenarios.
Conclusion
The purpose of jackpotting is to illegally extract money from an ATM. To do this, the attackers use personal devices that are connected to the ATM’s communication system. After gaining physical access to the ATM, the attacker disconnects the communication cable between the dispenser and the ATM computer in order to send it illegitimate commands to dispense cash.
To protect ATMs from jackpotting, banks need to regularly maintain anti-virus software, use hard drive encryption mechanisms and encrypted communication protocols, and take care to implement special ATM security solutions.
FAQ
What does ATM jackpotting mean for bank users?
ATM jackpotting does not lead to a leak of customer information. The purpose of such an attack is solely to obtain cash. The significant danger is that during the attack the criminals can not only empty the ATM, but also make changes to its functionality.
What is ATM jackpotting malware?
Malware is created to attack ATMs and enable attackers to obtain cash. Malware is infected after the physical security of the ATM has been compromised.
What software do ATMs use?
Any ATM is a computer with an equipment manager and a banking application. The CEN/XFS standard describes a server architecture consisting of an equipment manager and service providers that it manages. The banking application is designed to collect data from the user, send it to the host, and execute the response from the host. Modern banks prefer to equip their devices with solutions for ATM security, dispute resolution and fraud prevention.
What is an ATM skimmer?
A skimmer is a miniature portable reader that is attached to an ATM. More than half of all attacks on self-service devices are related to skimming, that's why banks implement special solutions to prevent this type of crime.

